How Proxyware Works
Proxyware Stops Online Scams
by Eliminating Threats at the Source
Organizations worldwide continue to increase cybersecurity spending, yet global cybercrime losses grow exponentially year over year. This imbalance highlights a fundamental flaw in how digital security has been approached: protecting systems while leaving people exposed. Proxyware takes a different approach.
Proxyware deploys undercover digital agents that act as a digital honeypot intentionally presenting as high-value targets such as a child, senior, veteran, or hospital patient. These agents attract predators and malicious actors before they ever reach real people. When attacks occur, Proxyware identifies, analyzes, and removes the threat at its source.
This diagram shows how Proxyware operates in a school environment. Traditional school cybersecurity protects networks and devices, but it is not designed to read website content, digital ads, or malicious media that specifically target children. As a result, administrators and adults often never see the harm because it is designed to reach students directly.
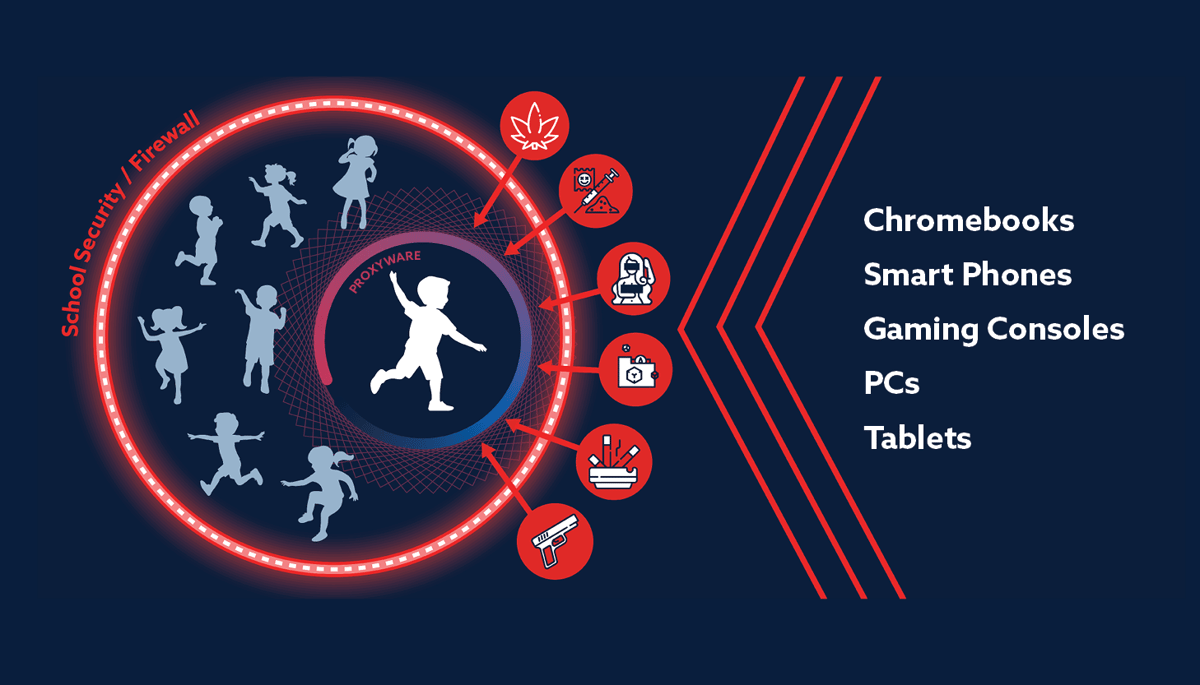
When a school deploys Proxyware, protection extends beyond the campus. Threats detected through that installation help safeguard students at home and in the surrounding communities by removing harmful content from the broader Internet.
Proxyware does not collect student information, browsing data, or personal details. No school data is accessed or stored, eliminating privacy, compliance, and parental consent concerns.
Detect. Remove. Report.
-
Simple, Non-Disruptive Installation. Proxyware installs quickly and easily without disrupting existing security systems. The solution requires only a dedicated computer for the Proxyware device to plug into—no network reconfiguration, specialized code, complex integrations, orperational burden on your IT team.
- Independent Operation with Zero Privacy Risk. Once installed, Proxyware operates independently and does not collect community data or personal information. Because no sensitive data is accessed or stored, there are zero privacy concerns and no compliance risk tied to data retention.
- We Become the Victim. Proxyware functions as a digital honeypot, deliberately presenting itself as a high-value target for attackers. Using hyper-realistic digital personas, Proxyware attracts predators, malicious advertisers, and threat actors before they ever reach real users.
- Threat Detection Across Shared Internet Infrastructure. When attacks occur, Proxyware identifies and analyzes the full attack path, including malicious third-party code, advertising supply chains, tracking technologies, embedded media, recommendation engines, and other reused components that enable harmful content to spread across trusted websites.
- Removal at the Source, Not the Endpoint. Proxyware removes digital harm at its source by notifying the companies unwittingly serving malicious content. This prevents the same threat from reaching other users elsewhere on the Internet.
- Proactive, Measurable Impact. This proactive approach enables Proxyware to eliminate 93% of harmful content it detects. By becoming the victim first, Proxyware prevents harm entirely rather than responding after damage is done. This creates protection that extends far beyond any single location, device, or organization.
- Monthly Insights from Our Digital Crime Database. Customers receive a monthly report detailing detected digital attacks and harmful content removed from the Internet, along with real-world examples and actionable recommendations.
